防止两个三层交换机长距离光纤线路被乱接测试
一.概述:
在论坛上看到有人想问通过什么方式来防止长距离的光纤线路被窃听,或连到其它非法交换机上,如是相同通过端口安全来实现防止乱接,于是登录机架进行测试,将测试结果记录下来。
----光纤线路,如果中间没有被恶意接入其他设备,应该很难窃听,因此觉得防窃听可以从防乱接方向入手。
二.基本思路:
A.假定交换机为三层交换机
B.如果两个交换机用三层口相连,并绑定对端IP所对应的mac,虽然可以防止接入三层设备,但是无法防止中间串接二层设备进行窃听。
C.通过主机之间的ipsec来加密流量,除非接线两端为路由器,否则两端连接交换机的主机太多的话,每台主机去配置IPsec不大可行。
-----高端的交换机没有玩过,一般普通的三层交换机貌似无法配置ipsec vpn
D.数据加密虽然是防窃听的最好方式,但是目前这种情况,貌似加密不容易实现
E.通过二层的安全来防止乱接:
---交换机相连的口采用access口,并且两端都配置VLAN的svi
---每个交换机保证用于互联的vlan只有一个互联接口
---三层交换机要开启路由转发,两个三层交换机互指路由(静态或默认),来实现交换机两边的PC互访
---配置互联端口的端口安全,只允许学习到2个mac,这样只有中间线路没有其他二层设备,当接入其他二层设备时,端口就会down,防止被监听
---本实验只是验证可行性,实际工作如果可能的话,还是建议用路由器互联,并配置ipsec。
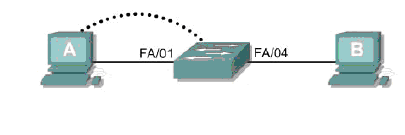
三.测试拓扑:

四.基本配置:
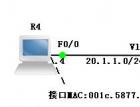
A.R4:
interface FastEthernet0/0
ip address 20.1.1.4 255.255.255.0
ip address 20.1.1.4 255.255.255.0
no shut
no ip routing
ip default-gateway 20.1.1.1
B.SW1:
ip routing
interface FastEthernet0/4
switchport access vlan 20
switchport mode access
switchport access vlan 20
switchport mode access
interface FastEthernet0/20
switchport access vlan 10
switchport mode access
switchport port-security maximum 2
switchport port-security
switchport port-security mac-address sticky
switchport access vlan 10
switchport mode access
switchport port-security maximum 2
switchport port-security
switchport port-security mac-address sticky
interface Vlan10
ip address 10.1.1.1 255.255.255.252
interface Vlan20
ip address 20.1.1.1 255.255.255.0
ip route 0.0.0.0 0.0.0.0 10.1.1.2
ip address 10.1.1.1 255.255.255.252
interface Vlan20
ip address 20.1.1.1 255.255.255.0
ip route 0.0.0.0 0.0.0.0 10.1.1.2
C.SW2:
ip routing
interface FastEthernet0/5
switchport access vlan 30
switchport mode access
switchport access vlan 30
switchport mode access
interface FastEthernet0/20
switchport access vlan 10
switchport mode access
switchport port-security maximum 2
switchport port-security
switchport port-security mac-address sticky
switchport access vlan 10
switchport mode access
switchport port-security maximum 2
switchport port-security
switchport port-security mac-address sticky
interface Vlan30
ip address 30.1.1.1 255.255.255.0
interface Vlan100
ip address 10.1.1.2 255.255.255.252
ip route 0.0.0.0 0.0.0.0 10.1.1.1
interface Vlan100
ip address 10.1.1.2 255.255.255.252
ip route 0.0.0.0 0.0.0.0 10.1.1.1
D.R5:
interface FastEthernet0/1
ip address 30.1.1.5 255.255.255.0
ip address 30.1.1.5 255.255.255.0
no shut
no ip routing
ip default-gateway 30.1.1.1
五.验证:
R4#ping 30.1.1.5
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 30.1.1.5, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/4 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 20.1.1.4, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 ms
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 30.1.1.5, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/4 ms
R4#
R5#ping 20.1.1.4Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 20.1.1.4, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 ms
R5#
sw1#show running-config interface f0/20
Building configuration...
Current configuration : 336 bytes
!
interface FastEthernet0/20
switchport access vlan 10
switchport mode access
switchport port-security maximum 2
switchport port-security
switchport port-security mac-address sticky
switchport port-security mac-address sticky 0014.a80a.f716 vlan access
switchport port-security mac-address sticky 0014.a80a.f741 vlan access
end
Building configuration...
Current configuration : 336 bytes
!
interface FastEthernet0/20
switchport access vlan 10
switchport mode access
switchport port-security maximum 2
switchport port-security
switchport port-security mac-address sticky
switchport port-security mac-address sticky 0014.a80a.f716 vlan access
switchport port-security mac-address sticky 0014.a80a.f741 vlan access
end
sw2#show int f0/20 | in Hardware
Hardware is Fast Ethernet, address is 0014.a80a.f716 (bia 0014.a80a.f716)
Hardware is Fast Ethernet, address is 0014.a80a.f716 (bia 0014.a80a.f716)
sw2#show int vlan 10 | in Hardware
Hardware is EtherSVI, address is 0014.a80a.f741 (bia 0014.a80a.f741)
Hardware is EtherSVI, address is 0014.a80a.f741 (bia 0014.a80a.f741)
sw1#show mac address-table | in 0/20
10 0014.a80a.f716 STATIC Fa0/20
10 0014.a80a.f741 STATIC Fa0/20
sw1#
10 0014.a80a.f716 STATIC Fa0/20
10 0014.a80a.f741 STATIC Fa0/20
sw1#
sw2#show running-config int f0/20
Building configuration...
Current configuration : 312 bytes
!
interface FastEthernet0/20
switchport access vlan 10
switchport mode access
switchport port-security maximum 2
switchport port-security
switchport port-security mac-address sticky
switchport port-security mac-address sticky 001a.a164.b216
switchport port-security mac-address sticky 001a.a164.b241
end
Building configuration...
Current configuration : 312 bytes
!
interface FastEthernet0/20
switchport access vlan 10
switchport mode access
switchport port-security maximum 2
switchport port-security
switchport port-security mac-address sticky
switchport port-security mac-address sticky 001a.a164.b216
switchport port-security mac-address sticky 001a.a164.b241
end
sw1#show int f0/20 | in Hardware
Hardware is Fast Ethernet, address is 001a.a164.b216 (bia 001a.a164.b216)
sw1#show int vlan 10 | in Hardware
Hardware is EtherSVI, address is 001a.a164.b241 (bia 001a.a164.b241)
Hardware is Fast Ethernet, address is 001a.a164.b216 (bia 001a.a164.b216)
sw1#show int vlan 10 | in Hardware
Hardware is EtherSVI, address is 001a.a164.b241 (bia 001a.a164.b241)
sw2#show mac address-table | in 0/20
10 001a.a164.b216 STATIC Fa0/20
10 001a.a164.b241 STATIC Fa0/20
10 001a.a164.b216 STATIC Fa0/20
10 001a.a164.b241 STATIC Fa0/20
---因为机架无法默认中间加入其它二层设备,但是可以通过往互联接口所在vlan添加其他接口来测试,因为接口收到其他mac地址的包,接口会down。
>更多相关文章
- 07-30路由器和交换器啥区别?你知道吗
- 07-30你所了解的三层交换机,是这样工作的
- 07-30你会使用交换机吗?连接交换机的正确方法
- 10-23黑客如何破解交换机密码
- 12-103228交换机VLAN配置
- 12-102618交换机版本升级实验
- 12-103228交换机STP配置
- 12-103228交换机链路聚合配置
首页推荐
佛山市东联科技有限公司一直秉承“一切以用户价值为依归
- 01-11全球最受赞誉公司揭晓:苹果连续九年第一
- 12-09罗伯特·莫里斯:让黑客真正变黑
- 12-09谁闯入了中国网络?揭秘美国绝密黑客小组TA
- 12-09警示:iOS6 惊现“闪退”BUG
- 12-25优酷推出U镜到底等直播功能 已应用在羽毛球
- 12-25百川智能正式发布全链路领域增强大模型
- 12-25SHEIN4家仓储物流园获“零废工厂”认证
- 12-25西方博主在TikTok上展现中国风貌,“China
- 12-05亚马逊推出新一代基础模型 任意模态生成大模
相关文章
24小时热门资讯
24小时回复排行
热门推荐
最新资讯
操作系统
黑客防御










 粤公网安备 44060402001498号
粤公网安备 44060402001498号